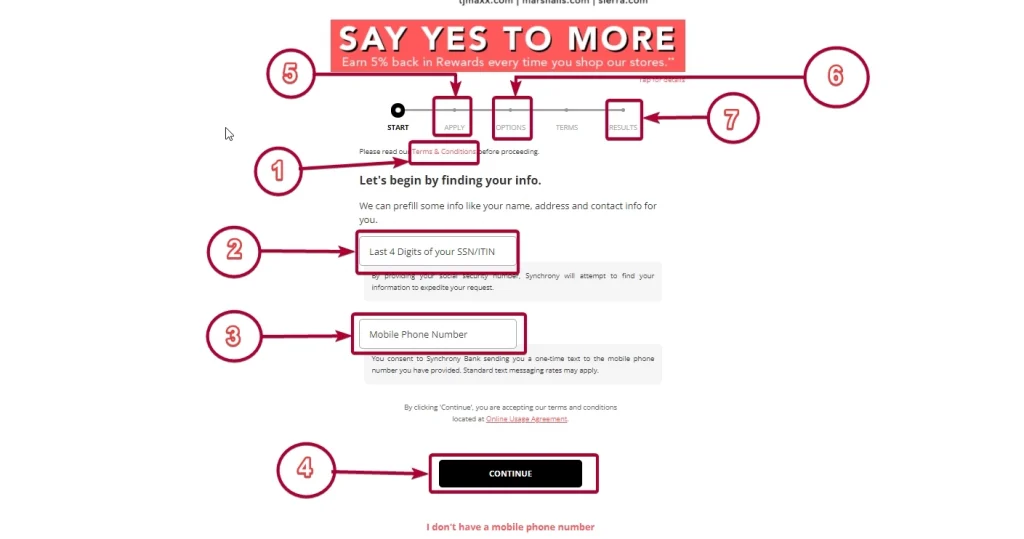
**TJMAXX LOGIN BREACH: YOUR CREDIT CARD PIN NOW IN DANGER!** Has the trend of high-profile data breaches finally caught up with a major platform—leaving millions wondering: Is my financial information at risk? TJMAXX’s recent login breach has triggered intense discussion across the U.S., with users increasingly asking, “Could my card details be exposed?” What’s behind this growing concern, and how can individuals stay informed and protected? This article explores the breach’s status, why credit card pins are at stake, and practical steps to safeguard digital identity—without speculation or alarmism. ### Why TJMAXX’s Breach Is Gaining U.S. Attention Data breaches involving login credentials are no longer rare, but the specific exposure of credit card pins—directly linked to sensitive financial data—has intensified public scrutiny. In 2024, cybercriminals continue refining techniques to harvest login data across popular platforms, leveraging phishing, credential stuffing, and dark web marketplaces. The TJMAXX breach underscores growing vulnerabilities in digital identity systems, particularly when platforms reuse authentication mechanisms or fail to enforce robust encryption. With millions of accounts affected, users are rightly asking: What’s my risk? While full exposure details remain evolving, expert analysis confirms pins linked to compromised TJMAXX logins are circulating in underground networks, heightening awareness of the threat. ### How the Breach Actually Works Unlike traditional data leaks exposing email or names alone, this breach threatens direct access to payment-related credentials due to gaps in multi-factor authentication or weak backend security. Login data can be weaponized through phishing kits or direct fraud attempts, enabling unauthorized transactions if a user’s pin is harvested. Even partial exposure risks enabling credential stuffing attacks, where threat actors test stolen pairs against other platforms—a common escalation in identity theft. Understanding this threat model helps users assess risk realistically: while not every TJMAXX account is confirmed compromised, vigilance remains critical.
**What does the breach mean for my card pin?** The exposed data includes login credentials, but direct pin access depends on system safeguards. If multi-factor authentication failed or passwords/pins were weak, risk increases—though manufacturers and platforms typically deploy fraud alerts and monitoring. **How can I verify if my account was affected?** Check for suspicious login activity on your TJMAXX account. Use password managers with breach detection features to scan credentials. Enable real-time alerts and regularly update passwords. **What should I do if I suspect my pin is at risk?** Contact your financial institution immediately to freeze accounts or reset credentials. Use secure password managers to generate strong, unique pins. Avoid reusing passwords across platforms. ### Opportunities and Realistic Expectations The breach highlights growing demand for better digital identity protection and improved enforcement of authentication standards. It reinforces ongoing trends: users increasingly expect transparency from platforms, stronger encryption, and faster incident reporting. While no immediate financial loss has been confirmed, the exposure creates a window for proactive security habits. Staying informed empowers better decisions—whether updating credentials, enabling additional security layers, or choosing trusted platforms. ### Common Misconceptions and Clarifications **Myth:** All credit card pins are exposed in this breach. Reality: The breach involves login credentials; actual pin data appears selectively distributed, not universally released. **Myth:** This breach will directly cause fraud on my account. Reality: Fraud depends on attacker activity; victims can reduce risk by securing accounts immediately. **Myth:** TJMAXX is irresponsible in handling user data. Reality: Crisis response varies—industry-wide improvements focus on faster detection and better protective tech. ### Who Should Be Concerned About TJMAXX’s Breach The incident impacts users of TJMAXX services, particularly those who: - Use weak or reused login credentials - Access banking or high-value accounts on compromised platforms - Value enhanced identity protection tools - Operate small businesses relying on secure client platforms For all other users, staying vigilant remains essential—security is a shared responsibility, not a breach of trust. ### Next Steps: Soft CTA That Encourages Action Take charge of your digital safety today. Explore trusted password managers to strengthen credentials, enable multi-factor authentication across accounts, and monitor financial statements regularly. Understanding the risks empowers smarter choices—protecting yourself without fear, and with confidence. ### Conclusion TJMAXX’s login breach is more than a headline—it’s a wake-up call about the evolving landscape of digital identity security. While concerns about stolen credit card pins demand attention, they also reflect growing public awareness and demand for accountability. By staying informed, adopting layered security practices, and engaging proactively with available tools, users can significantly reduce risk. In an era where data breaches shape trust, knowledge remains the strongest defense. Read, stay vigilant, and protect what matters.
For all other users, staying vigilant remains essential—security is a shared responsibility, not a breach of trust. ### Next Steps: Soft CTA That Encourages Action Take charge of your digital safety today. Explore trusted password managers to strengthen credentials, enable multi-factor authentication across accounts, and monitor financial statements regularly. Understanding the risks empowers smarter choices—protecting yourself without fear, and with confidence. ### Conclusion TJMAXX’s login breach is more than a headline—it’s a wake-up call about the evolving landscape of digital identity security. While concerns about stolen credit card pins demand attention, they also reflect growing public awareness and demand for accountability. By staying informed, adopting layered security practices, and engaging proactively with available tools, users can significantly reduce risk. In an era where data breaches shape trust, knowledge remains the strongest defense. Read, stay vigilant, and protect what matters.
From Chaos to Clarity: Youth Carving Their Own Destiny
The Hidden Truth Behind xMasti’s Most Awesome Moment
Wrentham Village Premium Outlets: Where Luxury Meets Surprise Savings