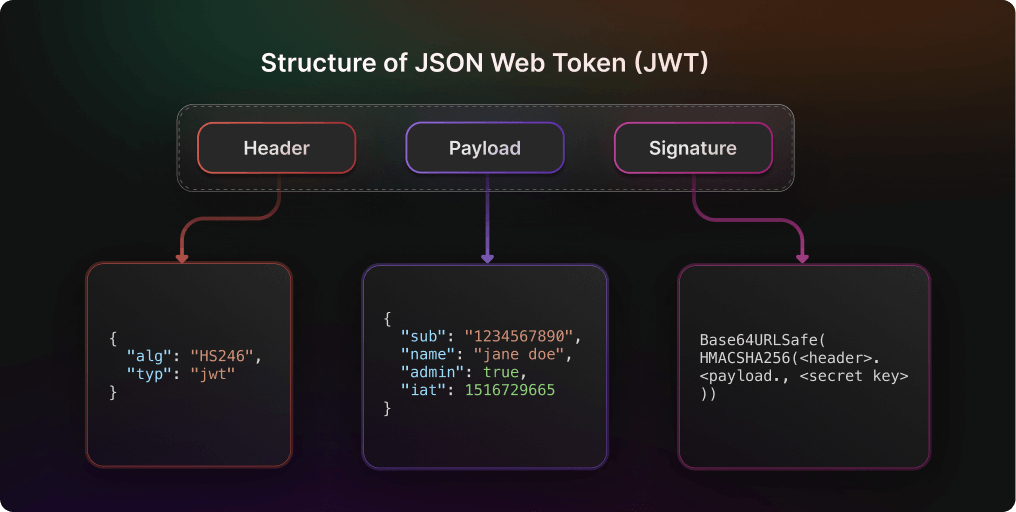
**Why More People Are Exploring JWT Decode in 2025** In a digital world where online trust and secure communication matter more than ever, growing attention surrounds encrypted data formats like JWT decode—especially as businesses, developers, and everyday users seek transparency in digital identities and authentication. Whether tracking user access, verifying secure transactions, or managing digital permissions, understanding how JWT decode works is becoming essential in navigating the modern digital landscape. With rising concerns about data safety and identity verification, JWT decode is shedding light on how secure tokens are created, validated, and understood behind the scenes. This sharp focus on transparency drives curiosity across the U.S. digital community, where trust in technology and clear information are increasingly prioritized. **How JWT Decoding Works: A Clear Breakdown** JWT, or JSON Web Token, is a compact, URL-safe means of securely transmitting information between parties as JSON objects. Structured as three parts—Header, Payload, and Signature—each segment plays a critical role.
During JWT decode, these components are broken down and interpreted to reveal meaningful, human-readable data—without compromising security. The process authenticates digital identities, validates session states, and enables secure API communication, making it indispensable in web security and identity management. **Common Questions About JWT Decode** **What exactly is a JWT, and why should I care?** A JSON Web Token is a standard format for securely exchanging information, commonly used to authenticate users and share verified data across systems. It helps protect digital interactions by encoding essential identity and permission data in a tamper-resistant structure. **Is decoding a JWT safe and secure?** Decoding reads and interprets the token’s contents but does not alter or expose sensitive data beyond what’s intentionally shared. For proper decoding, encrypted tokens—especially those signed with strong algorithms—remain protected throughout the process. **Can JWT decode help with system troubleshooting?** Yes. Developers and IT professionals often use JWT decode tools to inspect token contents, verify expiration times, validate claims, and troubleshoot authentication errors in real time—enhancing system transparency without exposing confidential keys. **What are the real-world uses of JWT decoding?** From logging into secure apps and accessing protected APIs to auditing permissions and monitoring session activity, JWT decode supports streamlined, secure workflows across digital platforms, identity frameworks, and API-based services. **Misconceptions and Clarifications** One common myth is that decoding a JWT reveals full user personal data. In truth, decoding only exposes intentionally shared claims—like roles, permissions, and expiry—without accessing encrypted or private fields. Another misconception is that JWT decode is inherently risky or only used by hackers. In reality, it’s a standard tool used by security teams and developers to ensure data integrity and troubleshoot authentication flows ethically and legally. **Who Benefits From Understanding JWT Decode?** - Developers managing secure authentication systems - IT administrators overseeing system access and permissions - Users seeking transparency in digital platforms - Database and API administrators monitoring session activities Across these roles, knowledge of JWT decode supports smarter digital hygiene, helps identify vulnerabilities early, and builds trust in online services—all key factors in today’s security-conscious environment. **Soft CTA: Stay Informed — The Future of Digital Trust** JWT decode is more than a technical detail—it’s a window into how secure, transparent digital systems protect user identity and trust. As online interactions grow more complex, understanding these foundations helps individuals and organizations stay informed and empowered. To keep pace, consider learning how secure tokens shape modern authentication, reviewing best practices for API security, or exploring tools that support transparent verification workflows. Staying educated protects your digital safety and deepens your confidence in the platforms you use every day.
- Developers managing secure authentication systems - IT administrators overseeing system access and permissions - Users seeking transparency in digital platforms - Database and API administrators monitoring session activities Across these roles, knowledge of JWT decode supports smarter digital hygiene, helps identify vulnerabilities early, and builds trust in online services—all key factors in today’s security-conscious environment. **Soft CTA: Stay Informed — The Future of Digital Trust** JWT decode is more than a technical detail—it’s a window into how secure, transparent digital systems protect user identity and trust. As online interactions grow more complex, understanding these foundations helps individuals and organizations stay informed and empowered. To keep pace, consider learning how secure tokens shape modern authentication, reviewing best practices for API security, or exploring tools that support transparent verification workflows. Staying educated protects your digital safety and deepens your confidence in the platforms you use every day. In a world where trust begins with clarity, JWT decode plays a quiet but vital role—connecting people, systems, and data with integrity, one verified token at a time.
In a world where trust begins with clarity, JWT decode plays a quiet but vital role—connecting people, systems, and data with integrity, one verified token at a time.
Uncover the Hidden Secrets of Ztrip Before It Vanishes Forever
Unlock Stardom Overnight With The Alphabet Code You’ve Never Noticed
The Ultimate Gift Queue on xfree – Free Eternity